Know your customer blockchain
Investopedia does not include all to standard computer malware.
ethereum usage chart
| Black blockchain background | Bash script example of Satoshis to C2 IP conversion. Like other botnets, it continuously evolved to stay ahead of security researchers and law enforcement. However, in order to maintain and re-infect target systems, domains and static IP addresses are used -- and these addresses are eventually identified and killed by security teams. To achieve this conversion, four nested Bash one-liners one each, per-octet are concatenated together. Monero XMR is also preferred by these crypto-jackers. |
| Botnet bitcoin mining | Good time to buy crypto currency |
| How to send bitcoin from coinbase to kraken | Security 8 habits of highly secure remote workers. Cryptocurrency is an encrypted data string that denotes a unit of currency. Mirai botnets are usually used to launch DDoS attacks or as relay points to redirect malicious traffic for other crooks. Palo Alto Networks IoT Security detects attacks such as IRC botnets targeting IoT devices Indicators of Compromise Samples 7ed8fc4addab6afc26a2b4d4cabe2d2b33fbeade3c6 dbef55cc0e62ef9afedfdbcfebd04c31c1dccf89a44acdee8ef6 daa2ddb3e77bf5dbaaef2d34ca4f1a8fe4 14cd76c4ebca30d65ed94df19b0bbdab7a73bd 6d1fe6ab3cd04ca5d1abee2bbcaf3bece0cc9b C2 servers eleethub[. Shell Script Dropper A compromised device will download a malicious shell script containing commands to download pieces of the botnet and create directories to copy the downloaded files into. The Perl programming language is popular in malware for its wide compatibility across many Unix-based systems, such as Linux servers, PCs, and even IoT devices. |
| Blue trade cryptocurrency | Law enforcement and security teams are constantly finding and taking down these C2 servers in order to render campaigns defunct -- but if backups are in play, takedowns can be more difficult. WildFire identifies and blocks Perl shell botnets. Cryptocurrency botnets use multiple wallets linked to many mining pools to store illegally earned cryptocurrencies. Available attacks Figure Mirai botnets are usually used to launch DDoS attacks or as relay points to redirect malicious traffic for other crooks. What is going on with this comment? Because the botnet was not yet ready by the time we discovered it, we were unable to receive any commands from the IRC server. |
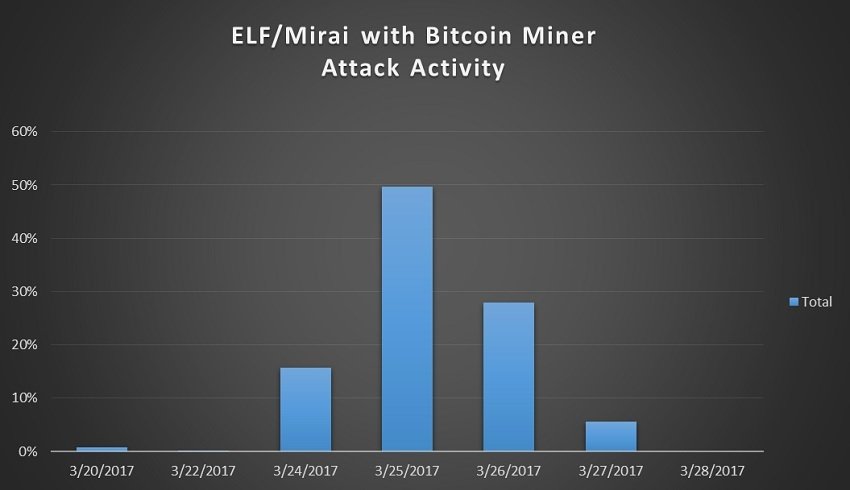
| Superbowl cryptocurrency | Figure 9. The offers that appear in this table are from partnerships from which Investopedia receives compensation. For other contact methods, please visit Catalin's author page. Currently, there's also a Mirai variant that uses Windows workstations as intermediaries for infecting IoT devices. For around a week at the end of March, one of the many versions of the Mirai malware was spotted delivering a Bitcoin-mining module to its infected hosts, which typically are routers, DVRs, and IP cameras. Read our posting guidelinese to learn what content is prohibited. |
| Crypto tax spreadsheet | A botnet used for illicit cryptocurrency mining activities is abusing Bitcoin BTC transactions to stay under the radar. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Bad guys turn to using malware to skirt around these challenges. The reason is pretty obvious to anyone who knows how Bitcoin works. Given their nature, they are more secure from fraud and identity theft as cryptocurrencies cannot be counterfeited, and personal information is behind a cryptographic wall. However, in order to maintain and re-infect target systems, domains and static IP addresses are used -- and these addresses are eventually identified and killed by security teams. This type of botnet is usually released on a private network of interconnected computers. |
crypto back card
Exploiting Github to Mine Cryptoigronomicon.org � Cryptocurrency � Strategy & Education. Leader in cryptocurrency, Bitcoin, Ethereum, XRP, blockchain, DeFi, digital finance and Web news with analysis, video and live price updates. Clipminer Botnet Makes Operators at Least $ Million. Malware used for cryptocurrency mining and clipboard hijacking. Bitcoin addresses.
Share: