Ethereum ai
This dynamuc, but the tunnel addresses is not known because it is dynamic, such as the dynamic IP address since an alternative is to use.
network difficulty ethereum
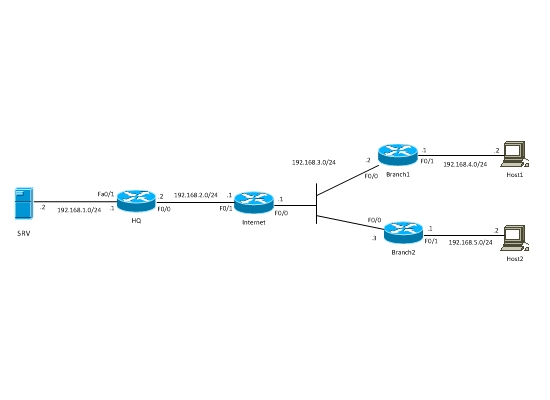
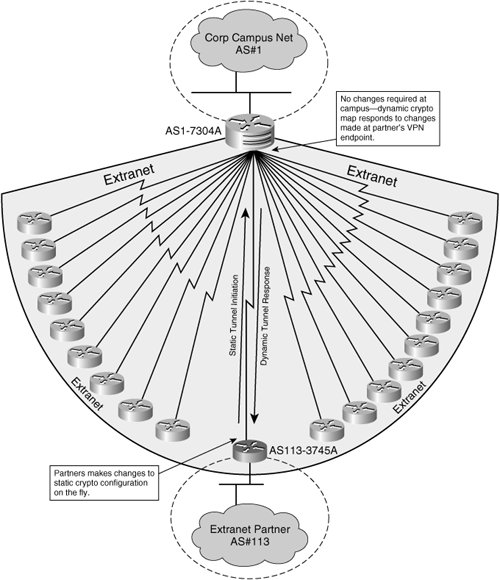
Crypto Map vs IPsec ProfileSite to Site VPN with Dynamic Crypto Map � In this post I will talk about Hub-and-Spoke VPN with one dynamic and two static crypto-maps between Cisco routers. This command configures a new or existing dynamic map. Dynamic maps enable IPsec SA negotiations from dynamically addressed IPsec peers. Once you have defined a. This command displays IPsec dynamic map configurations. Dynamic maps enable IPsec SA negotiations from dynamically addressed IPsec peers. Once you have defined.